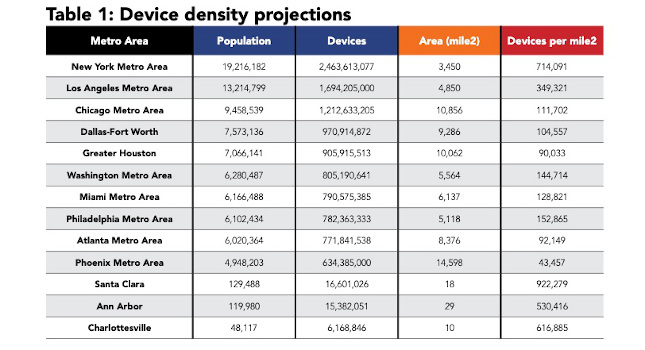
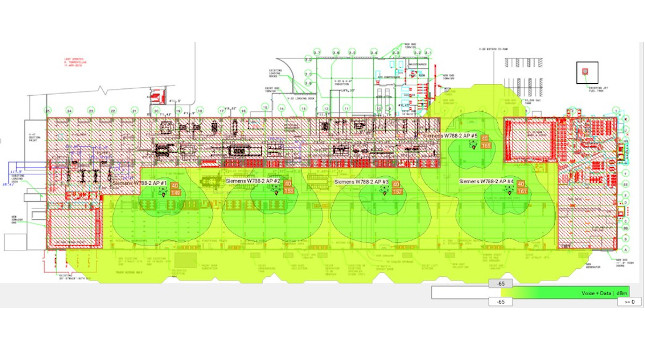
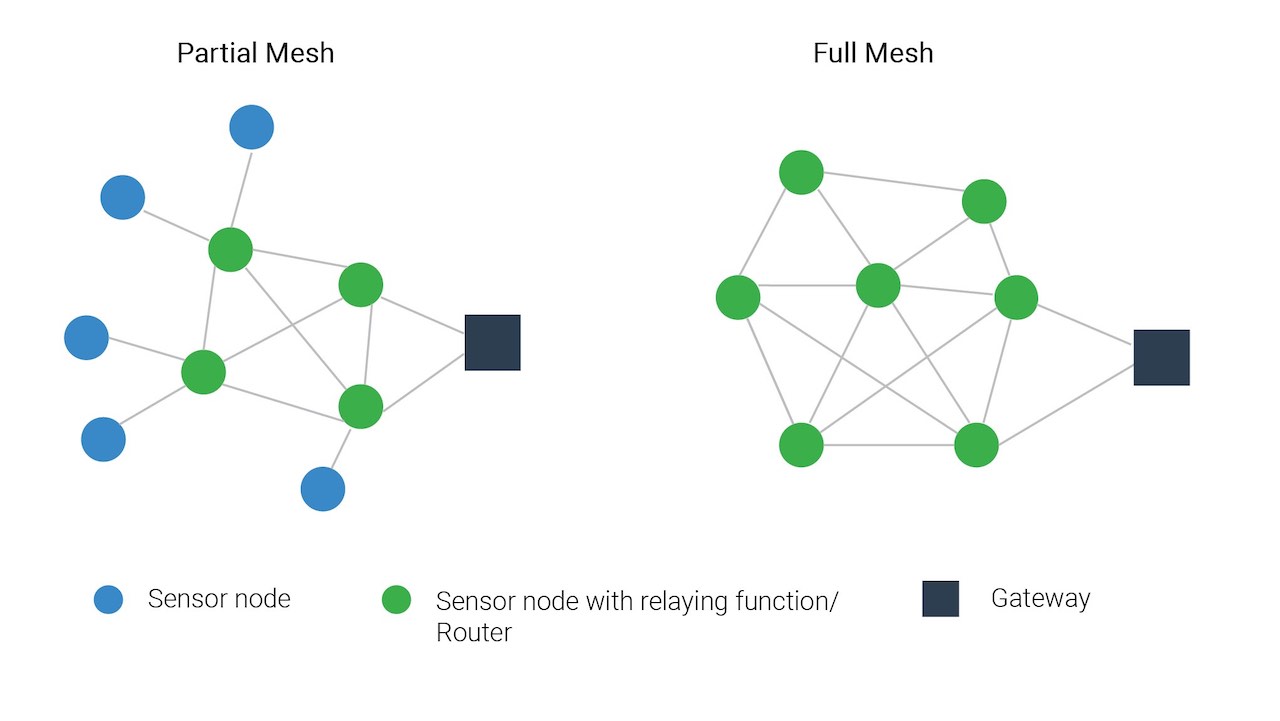
Wireless
Wireless refers to communication through the air between or among devices or systems. Wireless communications use a variety of standards and proprietary designs of the software and communications methods used for factory automation, process facilities and other industrial applications. Commercial standards, such as 4G or 5G wireless technologies, also are used.