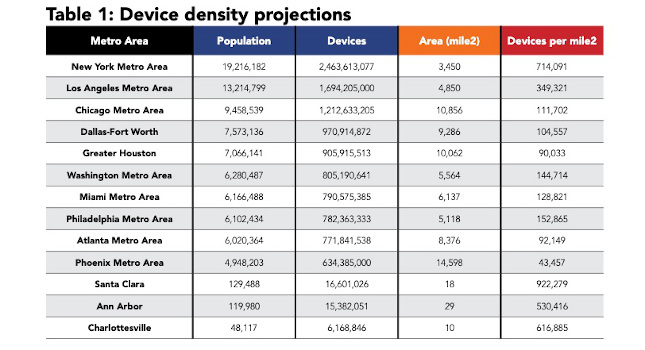
Does your data need to be stored in the cloud? Here are a few ideas to consider as you answer that question.

From the Sony cyber invasion to the intimate celebrity photo displays, recent events showcase the importance of preventing your valuable data from getting into the wrong hands now more than ever.
Yet many maintenance organizations still lack the IT resources, staff, and time to truly secure their own data based on industry and regulatory standards. As a result, reliance on Computerized Maintenance Management System (CMMS) applications hosted "in the cloud" are fast becoming the saving grace for maintenance departments around the world.
Modern CMMS solutions today offer a data hosting option, in which your data are typically managed by a third-party data center. Data centers manage the servers, storage systems, and more with all the protections and precautions in place to make sure that precious maintenance data are never lost or destroyed.
Good data centers not only host data for other companies, but must prevent downtime, respond to the unexpected, maintain security, and comply with government regulations. On top of this, data centers must maintain the HVAC, fire suppression systems, and redundant power and cooling systems, in order to be as efficient and effective as possible.
Depending upon your organization’s industry, policies, and other factors, external data hosting may not be an option for you. But for others, it may be the right way to go. Answer the questions below to see if your internal data management can keep your organization well-grounded, or if you should head to the cloud with a dedicated data hosting provider.
Can you guarantee the uptime of the computer servers that house your CMMS data?
Just as it’s essential to minimize downtime for equipment and building systems, so too, must data services remain up and running at all times. To ensure that availability, high-quality hosting providers offer 24/7 active monitoring. And when breakdowns inevitably occur, they must be able to restore data or fix problems in a matter of minutes – not hours.
That means the provider needs built-in redundancies and back-up systems to facilitate repairs and reduce interruptions from installing software upgrades or patches. Unless, of course, you have the resources to provide the same rigorous monitoring and backup.
Are you prepared for a natural or man-made disaster?
Because the idea has taken root in the popular imagination, it’s easy to think of data as floating in "the cloud," far above earth-bound problems. In reality, data lives on servers and it can hardly be "evacuated" when a blizzard moves in or a disgruntled employee shuts down your systems.
To evaluate the capabilities of a data hosting service, take a hard look at its disaster planning and protocols. Clearly, data that goes through one router to one server at one site is more vulnerable than information that’s backed up on multiple servers in several different locations that have an uninterruptible power supply.
Besides diversifying geographically to avoid service interruptions from natural disasters, providers of hosting services must also protect data from damage caused by fires, water leaks or floods, and temperature fluctuations – which means that cooling and HVAC systems have to be kept in top condition. Is your data ready for the next blizzard of the century?
Is your site secure?
Encrypting data as it travels around the data-sphere is certainly an important security measure for companies that want to protect their data from cyber attacks. At the same time, the physical plant that houses data hosting services must also be secure. That security may be ensured in any number of ways – such as employing keycard, biometric or badge scanning systems that limit access to authorized personnel; installing video cameras for ongoing surveillance and monitoring; establishing a lock-down environment for emergencies; and, in some cases, using armed guards to protect the facility.
Do you know what the security regulations are and can you pass an audit?
Data hosting providers are fulfilling a variety of compliance obligations and staying abreast of evolving regulations. A top-notch service provider will have a framework of policies, procedures and standards in place so they can maintain common industry audit certifications and ensure a high level of security. Those audits may be required by legislation or by industry specifications.
Examples include the HIPAA Security Rule, PCI (Payment Card Industry) Data Security Standard and the Service Organization Control (SOC) audits. A good security policy is based on common industry and government frameworks, such as Gramm-Leach-Bliley Act (GLBA) Interagency Guidelines, ISO or ITIL standards. Some data hosts take the extra step of conducting in-house or pre-audits to make sure they consistently comply with regulations.
Reliable service, high-grade security procedures, and ongoing regulatory compliance are all good yardsticks for measuring the quality of a proper data hosting service, whether this is handled inside or outside your organization. And, just as important, data management services should also be judged by how well they help a company meet their current and future needs for managing an increasingly valuable commodity: data.
– Paul Lachance is president and chief technology officer for Smartware Group, which produces Bigfoot CMMS. Lachance has been developing and perfecting CMMS for the maintenance professional for more than 20 years. Contact Paul directly at [email protected] or visit www.bigfootcmms.com. Smartware Goup is a CFE Media content partner. Edited by Joy Chang, digital project manager, CFE Media, [email protected]