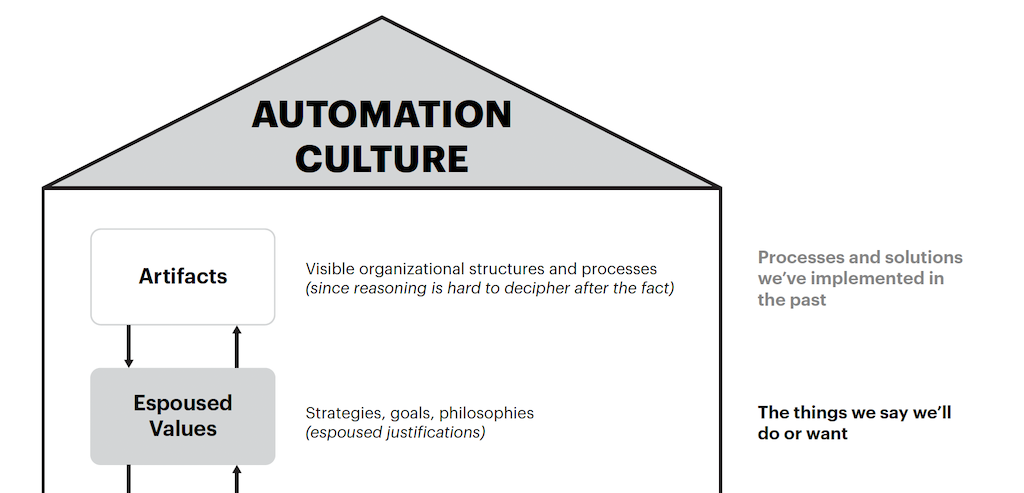
Back to Basics: Industrial control systems (ICSs) are becoming a more frequent target for cybersecurity attacks, and companies working in vital industries need to take steps to prevent or reduce the risk for a catastrophic event. See five drivers of and eight ways to support ICS cybersecurity.
Significant security risks and attacks against industrial control systems (ICSs) are growing in volume, and comprehensive solutions are needed. The financial and legal ramifications of breached ICSs are mounting across the world, and regulators are increasingly interested in a company’s ability to defend against cyber attacks. The fragmentation of partial solutions and the complex integration of these are becoming a cost, and risk owners want to mitigate.
Threats and cyber incidents—malicious and accidental—against ICSs occur every day. These systems are a critical part of the infrastructure that facilitates operations in vital industries such as power generation, oil and gas, transportation, pharmaceutical, and chemical. In the past, ICSs operated in an environment that appeared safer because they were physically isolated and used proprietary control protocols with customized hardware and software.
Five cybersecurity drivers
Cybersecurity solutions are increasingly designed for operations and policies, and there are five key constituents that can drive targeted solutions for ICSs:
- Audit and application of security policies and procedures developed specifically for the control system network and its devices
- Access control through the local area network (LAN), wide area network (WAN), and physical perimeters complemented with secure data transfers
- Threat detection of abnormal and malicious activities at all levels
- Risk management and mitigation against possible attack with an installed security suite designed to enhance regulate the ICS without disrupting the controlled process.
- Resolve key security problems that require an intrinsic relationship with vendors.
The ICS represents the core of production, which means the cybersecurity processes must address internal and external threats with multiple layers of defense that mitigate against various risks.
Initiatives by ICS vendors to reduce security risks to control systems in response to growing cybersecurity is resulting in automation professionals being more effective in securing their industrial processes. However, ICS vendors and automation professionals must be committed to providing a set of products and services that mitigate risks and provide security for production assets. And, the information silos that exist within organizations mean information is rarely shared. Comprehensive solution providers will acquire, integrate, and facilitate the adoption of cybersecurity technologies and deliver the product to end users.
Because ICSs are prone to cyber attacks and are being targeted with increasing frequency, automation vendors are working with information technology (IT) security service providers to develop stronger solutions. While many of the vulnerabilities are technology-based, it is worth noting that some weaknesses stem from a lack of personnel or a lack of awareness. These changes may require cultural shifts and collaboration mechanisms to reduce mistakes caused by human error.
An organization’s risk management practice must be proportionate to the risks present. Organizations should not be asking, "Is there a risk," but rather "Which risks do we face and what is the level of investment to mitigate against them?" Educating executives and staff has not kept pace with the continually changing cybersecurity threats. Corporations must get involved in workgroups that discuss the current cybersecurity situation in their sector, describe key strategic elements to increase their security posture, and support workers with tools and guidance.
While the industrial sector is slowly recognizing there is a greater cybersecurity risk for ICSs, risk management is difficult due to the high costs linked to each risk and a lack of historical statistics to determine the probability of the scenario occurring. Companies must have cost-effective and efficient solutions that will keep industrial facilities safe. This is critical to the global economy.
This is why organizations must have their policies and procedures in place with security designed and implemented within the ICS environment before any further integration into other networks. The business case, security posture, and risk management plan determine the protocols and methodology for systems integration.
Another factor to consider from this systemwide integration is that IT security professionals do not properly understand the industrial processes that utilize the ICS, and ICS professionals do not properly understand today’s IT security risks. This can result in a lack of awareness and safeguards that will take away from the benefits that were sought through the integration of the business and control systems when one major ICS incident occurs.
Cybersecurity support
With that in mind, the following objectives should be met to support the ICS’ security components:
- A framework that provides an overview and identifies the core elements
- Corporate-level governance to ensure security risks are managed consistently and appropriately
- Thorough understanding of the risks that are faced and ability to justify the mitigation response needed
- Management of the ICS lifecycle that follow a security engineering process
- Improved ICS security awareness throughout the organization
- Continuous review of security protection measures that can be selected and implemented
- Procedures that deliver a sufficient response to new vulnerabilities and changes to the threat environment
- Effective management of third-party risks that can have an impact on the organization.
Anil Gosine is global program manager at MG Strategy+. Edited by Chris Vavra, production editor, Control Engineering, CFE Media, [email protected].
MORE ADVICE
Key concepts
- Comprehensive solutions are needed to prevent attacks against industrial control systems (ICSs).
- Automation vendors are working with information technology (IT) professionals to craft potential solutions.
- There is a lack of understanding between IT and ICS professionals, and that can lead to security issues.
Consider this
What else can be done to close the gap between ICS and IT professionals?
ONLINE extra
See additional stories about industrial control systems (ICSs) linked below.