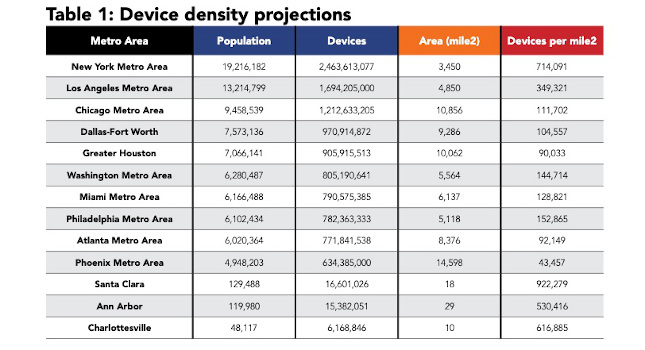
The Industrial Internet of Things (IIoT) offers many potential benefits, but it also poses many potential risks from a cybersecurity standpoint, and many companies are slow to realize this drawback.
Talking about the Industrial Internet of Things (IIoT) is at such a fevered pitch not seen in the industry in a long time, or if ever, but what users and vendors alike need to understand is security needs to be a major part of the discussion—and it appears it is not. The IIoT offers great advantages if properly implemented, but there is great danger if implementation is done wrong.
IIoT products are hitting the market at such a rapid manner it has gotten to the point where there is a smart anything going out right now. In the IIoT the hope is users have matured enough to realize by adding in intelligence and more connectivity there should be added security.
"Vendors of the products for mainstream controls companies have spent a lot of time and effort trying to figure out how to secure their programmable logic controllers (PLCs), distributed control systems (DCSs) or drives," said security controls expert Eric Byres. "Now we have all these other little ‘things’ makers and security is not even on their radar. They are probably good product engineers;
they have a product, and they are making them an IIoT product by putting in a chip, an Ethernet interface, and a web server, [and] they say we now have an IIoT product. In my experience, they say, ‘security, what security?’ For security, they say the client should keep it off the Internet. They take a product, and try to make it an IIoT product, and security has not even come into their wheelhouse."
That all falls back on thinking about security from the outset. In the rush to get to market, no one is thinking security.
"Nobody stopped to think about the impact," Byres said.
Going to market
If the marketing hype is to be believed, there has been a rush to get to market, and that could end up as an issue within the industry if users don’t force "things" suppliers to ensure a secure product.
"I believe the original intent was to make IIoT mean it was an industrial system which encompassed reliability and security, amongst other things," said Graham Speake, CSO at Berkana Resources Corp.
"While some companies might be designing systems to meet these goals, the drive to get new and innovative products out the door is often causing the additional engineering needed to produce a secure solution being shortened or curtailed altogether. Often the need to be seen in this (IIoT) space as a leader is more important to companies as they know the sales cycle can be long, and features (such as security) are often perceived as being able to be added if the end user demands them."
That means IIoT right now could be a security runaway train.
"IIoT is something that is being adopted regardless of security," said Yoni Shohet, chief executive at SCADAfence. "It is being adopted because it saves these industrial companies money. Whether these architectures or networks are secure or not is not relevant to decide of they will adopt or not. They will adopt. The question is how well will they secure them after they adopt."
The good news is security awareness level is higher than it has ever been, so a user understands the talk about securing his or her system at the plant and over the Internet.
"Vendors supply basic security, but it is not enough. It is also the people and organizations adopting the products. It needs to be a combination of both. It is about having the right people and right policies on the job for IIoT security," Shohet said. "We are seeing an increase in IIoT products that increase productivity regardless of the level of security. I don’t think there are a lot of companies that will stop an integration that can save them a lot of money because they think it is not secure. It is part of an awareness of potential risk. I think they understand the risk at a very basic level."
Already there
The interesting thing about the IIoT comes from all the mini devices that were not intelligent until recently, and security for those devices is different. They end up using unsecured protocols. They have a small amount of software, processors, and a tiny amount of memory. If security ends up built-in, then there is no problem, but if it is not, then there will be cases where hackers can end up manipulating things remotely over the Net.
While the IIoT hype has ramped up, the actual technologies behind it have been around the industry for quite some time as intelligent control devices that have been interconnected. Look at the smart grid. The challenge comes when a user ends up tying all this connectivity, data collection, and intelligence with things like cloud services, and this connected network of things that once lived well within the confines of the company’s network, is now a part of the Internet. That means the attack surface just skyrocketed.
"IIoT is in many ways already part of the industry and has been for the last decade," Byres said. "After all, what are all those RTUs and IEDs in substations and on utility pole tops if not ‘Smart, Interconnected Things?’ What are all those EtherNet/IP drives and sensors? The big change/threat is in:
- The number of new and different ‘things’ being integrated, especially from vendors traditionally separate from the actual control functionality
- The scale of the interconnections
- The attention industry is now getting from ‘bad actors’ like the people responsible for the Ukraine blackouts or Dragonfly"
"All these changes require a different way of looking at industrial control system (ICS) security, instead of the obsolete bastion model (aka ‘electronic security perimeter’ in NERC CIP) particularly popular in power industry security regulation today," Byres said. "When your ‘security cameras’ tunnel through your firewalls to connect to a site in China, it has to be 100% certain your control network is not ever connected to the Internet."
Gregory Hale is the editor and founder of Industrial Safety and Security Source (ISSSource.com), a news and information website covering safety and security issues in the manufacturing automation sector. This content originally appeared on ISSSource.com. Edited by Chris Vavra, production editor, CFE Media, Control Engineering, [email protected].
ONLINE extra
See additional stories from ISSSource about cybersecurity below.